📧 Mail Security? What Security?
🤔 Once Upon a Time in SMTP...
Remember when we designed email protocols? Yeah, me neither - I wasn't born yet. But apparently, someone thought it would be a great idea to create a system where everyone can pretend to be anyone else. Fast forward a few decades, and we're still dealing with the consequences of these "it's fine, everyone on the internet is trustworthy" decisions.
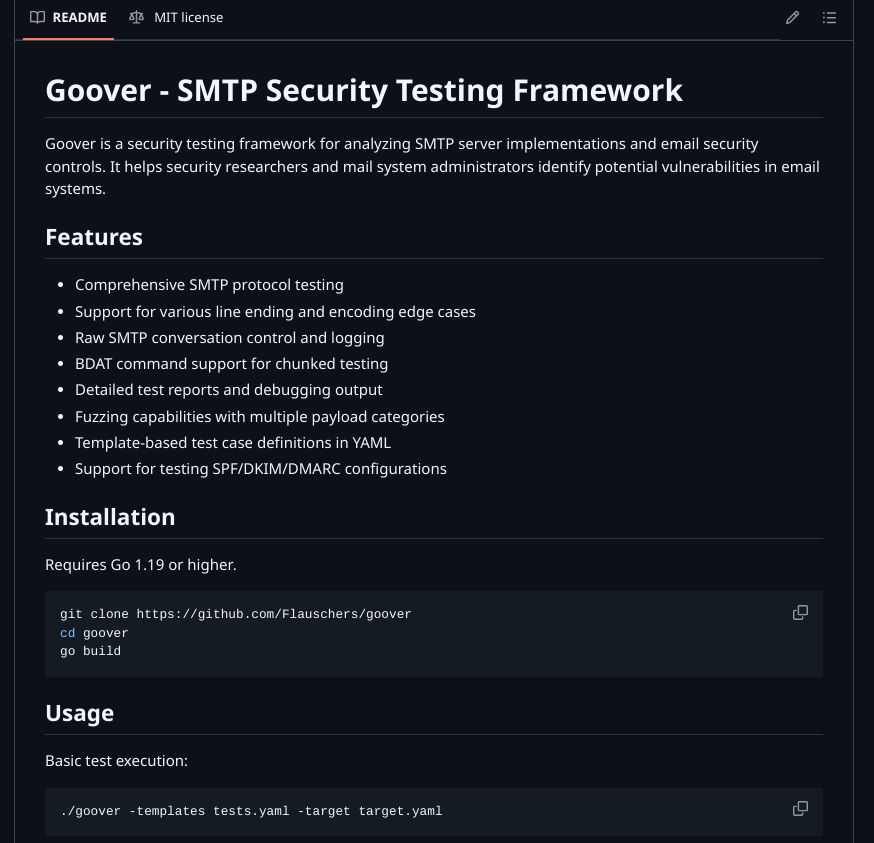
🛠️ Enter Goover: Because Why Not Break Things?
Recently, I've been playing around with a little tool I created called "Goover". It's like a Swiss Army knife for SMTP testing, except instead of helping you open wine bottles (which would probably be more useful), it helps you understand just how fragile email security really is.
🎯 The Results Are In (And They're Hilarious)
Within just a few hours of testing, Goover managed to successfully:
- Send emails appearing to come from legitimate domains
- Bypass SPF, DKIM, and DMARC in various ways
- Make email clients and servers disagree about who actually sent an email
- Prove that parsing email headers is apparently harder than quantum physics
And the best part? These aren't even sophisticated attacks. We're talking about basic stuff like:
- Adding some spaces here and there
- Playing with line endings (because apparently \r\n vs \n is still a debate in 2024)
- Making headers do gymnastics
- Sneaking in some invisible characters (because if you can't see it, it can't hurt you, right?)
🤦♂️ The State of Email Security
You know what's really fun? We've built entire business infrastructures on top of a protocol that can be confused by a well-placed space character. It's like building a bank vault but making the door out of papier-mâché because "that's how we've always done it."
SPF, DKIM, and DMARC were supposed to be our saviors. They're like security guards who are really good at checking IDs, except they can be distracted by someone saying "Look over there!" Meanwhile, the actual email just walks right in through the back door.
🔬 The Technical Bits
Goover is built in Go (because we're modern like that) and uses YAML templates to define test cases. It's like a recipe book for email spoofing, except instead of making cookies, you're making security engineers cry.
The tool includes:
- A raw SMTP client (because sometimes you need to speak directly to the server)
- Fuzzing capabilities (for when you want to really ruin someone's day)
- Detailed reporting (so you can prove it wasn't your fault)
💼 The Business End
So, now that I've thoroughly destroyed your faith in email security, how about we talk about fixing it? Because if there's one thing better than breaking things, it's breaking things and then charging to help fix them.
I offer professional security assessments where I:
- Break your email security (professionally, with a report and everything)
- Show you how broken it is (with pretty diagrams)
- Help you make it less broken (no guarantees about completely fixing it because, well, it's email)
🤝 Let's Talk
If you're now appropriately concerned about your organization's email security (as you should be), let's have a chat. Head over to https://dreher.in/contact and let's discuss how we can make your email security slightly less terrible.
Remember: In a world where email security is held together with digital duct tape and hope, the best defense is knowing just how bad it really is.
P.S. No email servers were permanently harmed in the making of Goover. They just had their feelings hurt a little bit.
I may release the tool later, but for now I am going to hunt for some CVEs first 🏆