Howto run dockerized MobSF with Dynamic Analyzers
pentesting
Recently I discovered my love of using docker to organize all my stuff.
But accoring to the MobSF Documentation Dynamic Analysis is not supported by running MobSF inside of docker.
But after looking on how the MobSF guys built the docker image, especially how you can use external environment parameters to configure the runtime of the MobSF inisde of docker.
There was only one thought

1. Get an Android emulator supported by MobSF
MobSF Documentation explains in details how this works and which is supported.
I think there are only two requirements which must be fullfilled:
- Android must be reachable by ADB over network
- Frida must run
Also if you wanna use my simple solution, there must be an easy way to retrieve the IP addresse of your Android emulator on the command line. In my case I make use of Genymotion Android x86_64. The Desktop version of Genymotion is based on VirtualBox.
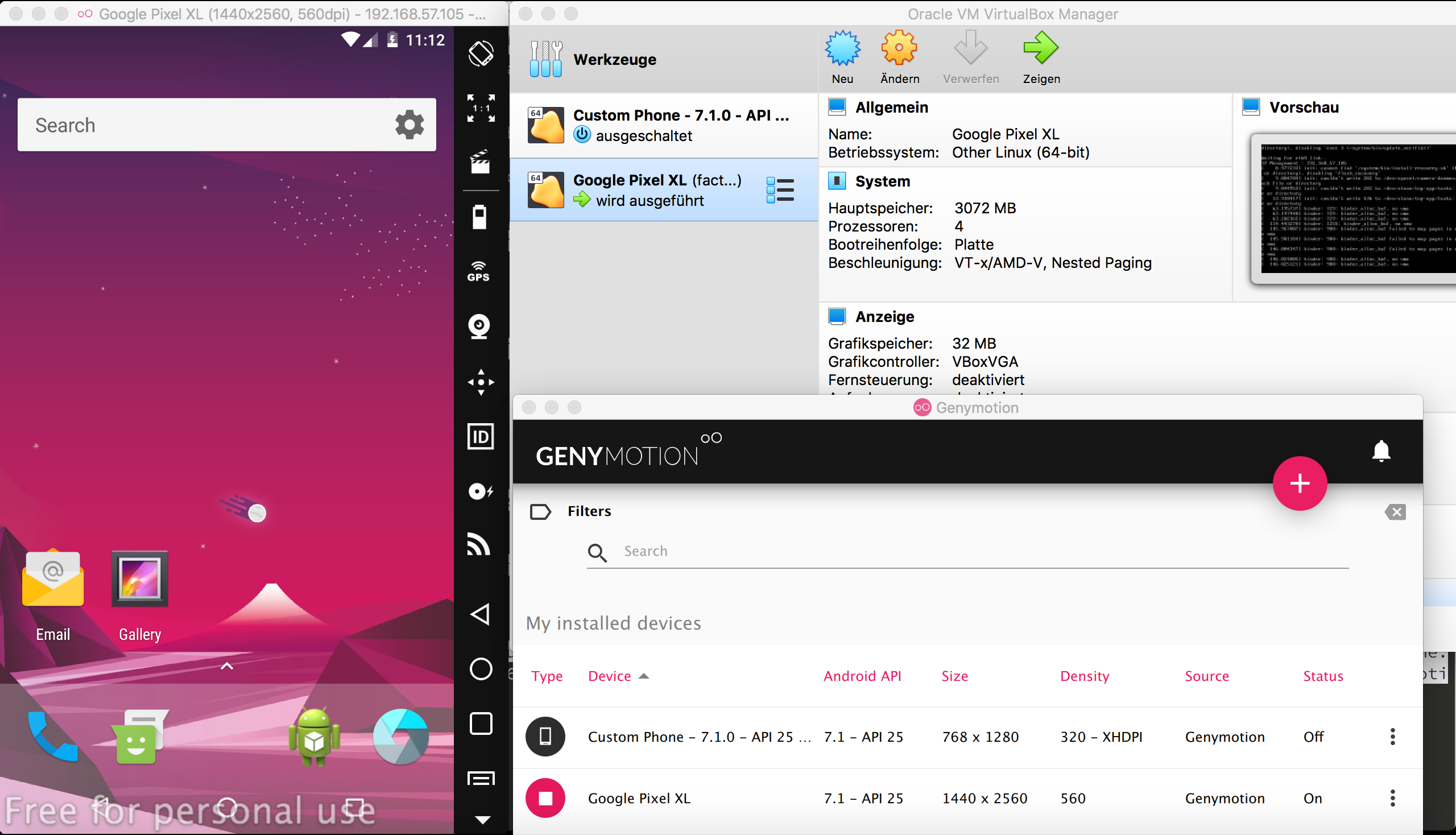
2. Fetching the IP address of the emulator
As Genymotion is based on VirtualBox, we can use the VirtualBox command line interface to retrieve the IP address of the Android emulator:
$ VBoxManage guestproperty enumerate "Google Pixel XL" | grep androvm_ip_management | awk -F',' {'print $2'} | sed -e 's/ value: //g'
$ 192.168.57.105
ABove command fetched the IP address of my emulator called "Google Pixel XL" (see also Genymotion screenshot above). Ok now there is only one last thing todo.
3. Connecting your dockerized MobSF with the emulator
$ docker run -it -p 8000:8000 -e ANALYZER_IDENTIFIER="$(VBoxManage guestproperty enumerate "Google Pixel XL" | grep androvm_ip_management | awk -F',' {'print $2'} | sed -e 's/ value: //g'):5555" opensecurity/mobile-security-framework-mobsf:latest
MobSF is up and running and available at http://localhost:8000.
4. Mobsifying the Android emulator
Before MobSF can make use of your new wonderful dynamic weapon, the Android system must be prepared, eg. installing Frida. Luckily, the MobSF guys did a really great job here too. The only thing you have to do is to click the "MobSFy" button.
And within your docker log you can also see whats happening in detail:

Congratulations. You have now a dockerized MobSF ready to analyze all the things dynamically.
